Storing login information on the mobile web
One of the big advantages that native apps have over mobile web sites is that native apps never ask you to login again and web sites do. Why is that?
Let’s look at a very specific example of a site and app that I use on a regular basis—the Alaska Airlines app and mobile site.
Because I travel a fair amount, I have found myself using both Alaska Airline’s iOS app and their mobile web site quite a bit.
I end up using both because neither does exactly what I need. The mobile web site will tell me where I am on the upgrade waitlist, but the app won’t. And while the app doesn’t have all the data I need, it doesn’t log me out which means I don’t have to dig up my password to find any of the information that the app provides.
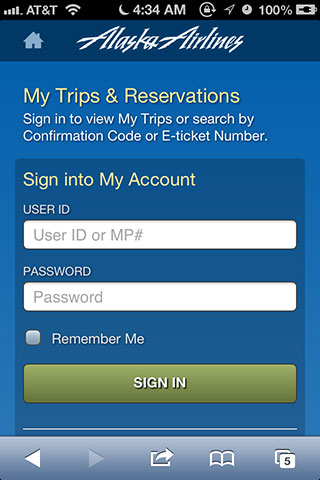
I would prefer to use the mobile web site. There are a few things that I like better about the mobile web site than the app and I get some data, like the upgrade list, that I don’t have in the app.
Despite my inclination, I find myself using the app more often because I don’t have to worry about supplying a password.
Which brings me to my question: why do I need to continually log into the mobile web site and not the app?
There is nothing that prevents a website from keeping me logged in indefinitely. If it is for security reasons, then wouldn’t those same security reasons apply for the native app?
I’m honestly confused by this. It isn’t just Alaska Airlines that I see making different decisions about how long they store credentials in apps versus mobile web sites. Does anyone have a good reason why this might be the case?

Jason Grigsby is one of the co-founders of Cloud Four, Mobile Portland and Responsive Field Day. He is the author of Progressive Web Apps from A Book Apart. Follow him at @grigs.